When an excavator cuts through an internet line, the lack of an adequate fail-safe system and system redundancy, especially in security technology, leads in many cases to considerable damage and long-lasting effects. Guaranteeing reliability is not difficult. The key here is the connection. Mobile connectivity and LTE backup systems offer a better option than using cables vulnerable to physical damage!
90% of our customers and partners have asked themselves the following questions:
- How do our services and security systems, remain in-service in an emergency?
- Is our company sufficiently protected?
- What measures are important to ensure “resilience”?
- Is the issue of “reliability” taken seriously? Or are we even aware of its importance?
- How costly is an outage and can we afford the consequences?
This leads to serious questions for manufacturers regarding their dependence on security systems and equipment.
Their aim is to ensure the reliability of their own products and systems and thus ensure that their end customers can depend on their reliability.
The decisive key to avoid disruption and maintain operational reliability is the connection. In this case, mobile connectivity provides a better option than vulnerable cable connections.
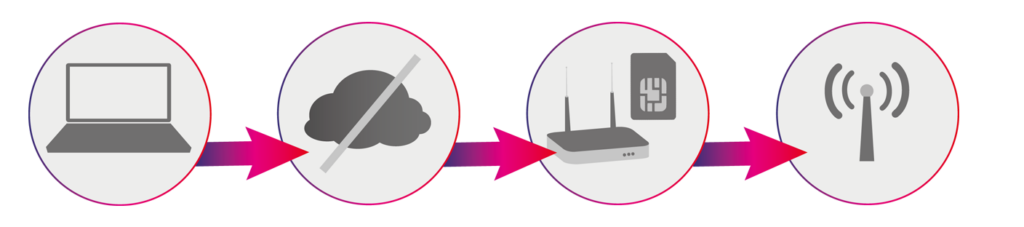
What characterizes reliability and redundancy?
If a system or application breakdown leads to undesirable consequences, then reliability should be the most important criterion when designing and procuring new systems or optimizing and further developing these systems.
When dealing with critical systems, there are various factors which must be fulfilled to achieve a fail-safe mode:
- Availability
- Redundancy
- Robustness
- Recoverability
- Scalability
- Security
- Monitoring and diagnosis
Availability describes how reliably a system functions and can deliver the required services.
In contrast, the redundancy of a system describes whether the system contains parallel components that can replace each other and thus minimize the risk of breakdowns, e.g. through an LTE backup.
If an application can also deal with faults, and repair and restore itself, this is referred to as robustness and recoverability.
The scalability of a system is also important for ensuring protection against breakdown. This describes whether a system can adapt to changing requirements without losing reliability.
The security factor indicates whether a system is protected against access by unauthorized persons and attacks of various kinds.
To ensure the reliability of an application, it is also important how well a system can be monitored and diagnosed. The decisive factor here is whether problems can be identified and rectified at an early stage.
If these seven factors are fulfilled, a device or system can be said to be fail-safe.
The challenges behind reliability
The secure use of devices and systems in small, medium-sized or even large companies, for example for the security of people, buildings and objects, depends on their connection to the data-transmitting equipment. These can be mobile or based on fixed data transmission paths, such as copper or fiber optic cables.
If a disruption occurs, e.g. if a vital cable is cut during construction work, a smooth-running operation without serious consequences is only achievable under one condition: if at least two different solutions are being used in parallel for data transmission, so that one can replace the other in an emergency. Redundant (security) technology is therefore required. A backup, so to speak, is required for the system which is in normal use. Internet of Things (IoT) solutions are ideally suitable for this.
Let’s put it this way:
Today more than ever, companies are dependent on reliable and secure internet/data connections and the consistent operation of their security systems. If these fail for any reason, the company’s systems may go down and they will have to wait, perhaps for a considerable amount of time, for a technician to reach the site and fix the problem.
The business’s inability to function is often due to the fact that not only business data is affected by the outage, but also because many operating systems and processes are partly or completely linked to these data connections. The consequential losses should not be underestimated.
How costly are outages and can I afford the consequences?
Accidental damage to pipes alone leads to considerable costs every year. Pipes for wastewater, power lines, broadband cables and other buried services are often laid very close to each other. Identification is difficult as there is usually no complete site plan available. Around 100,000 damage claims with a value of approx. 500 million euros are received each year. Experts suspect that the actual sum is probably much higher. In addition to the unclear liability situation, the losses to the affected companies for business interruption are not stated. (Source: Meistertipp, 2020)
This gives a good impression of how expensive accidental damage alone can be, without including deliberate damage. However, the direct consequences for companies are usually much more serious. A shutdown has an enormous impact. Even if the downtime is short, this quickly has a negative effect on turnover.
Another factor that should not be underestimated is the impact of such an outage on the brand image of the company. As the GBB flash survey (2019) shows using the example of the banking and financial services sector, damage to image should not be underestimated. At 25%, loss of reputation is perceived as the greatest risk, ahead of data loss at 23.8%. The reason for this is that companies are dependent on their customers and employees. If credibility and trust in the company concerned fall, it is not uncommon for future sales to fall as well.
Protection against this is not necessarily expensive. If an outage lasting several hours is not critical for your company, then the investment required in redundancy to maintain reliability does not need to be high.

The route to safety with LTE backup
The potential consequences of systems outages lead us to make a clear recommendation: use at least two independent, redundant systems or equivalents that “stand in for” each other. In some cases, this is mandatory by law. Potential scenarios for equipment breakdown and systems outages should therefore already be planned for in the design of the security equipment and the appropriate solutions for the respective systems processes.
Companies often start taking precautions too late – frequently only after something serious has happened and damage has already occurred. Instead, a company should undertake a risk assessment analysis and subsequently develop and implement appropriate fail-safe concepts and solutions. Based on our experience, it is better to start with the worst-case scenario in order to determine the safest way to avoid a shutdown.
Trust is good – verification is better
There are several ways to ensure a fail-safe internet connection:
1. the two-way solution or multiple protection:
This requires several connections. For example, different cable connections, e.g. fiber optic and coaxial cable, which do not use the same cable routing.
2. the solution via LTE backup / mobile backup
You can also use a combined two-way solution consisting of a fixed network and a mobile-based backup solution!
How systems providers can ensure fail-safe solutions
As a supplier of systems that can classed as security systems, there are a number of things to consider in addition to legal requirements. The supplier must design the security systems in such a way that users are optimally protected against system breakdowns and that as little additional effort or additional equipment as possible are required to ensure this.
This means that suppliers should develop security systems to meet advanced hardware, software and service standards. The products must also meet all safety, robustness, reliability, redundancy and availability requirements. Devices with new or additional performance characteristics or features may have to be developed in order to be able to process data, voice and SMS. In particular, the hardware and software must be able to manage higher bandwidths and data volumes. Suppliers should also check whether specific certifications are required in order to meet the regulatory standards.
The development and enhancement of existing systems also provides an opportunity to tap into new customer target groups. The targeted testing of new usage and billing models using IoT systems as a backup also opens up new revenue potential for systems providers. This makes it possible to develop a customized business model based on FUSION IoT.
The way to achieve this is very simple: ensure greater security, avoid disruptions and automate processes.
Fail-safe IoT systems and security technology use cases
These business cases use reliable LTE backup systems. This means that the on-site services can continue to operate safely in hazardous situations or in the event of damage to transmission systems.
Video surveillance
The classic: video surveillance is already frequently used by private individuals and companies. In addition to monitoring buildings, it can also be used in (remote) locations.
There are a number of advantages to using video surveillance systems, especially when they are combined with other security systems. The advantages include:
- Image and sound recordings can be stored digitally
- Software can be used for the purpose of facial recognition or license plate recognition
- Crimes can be solved through recordings (course of events, persons, etc.)
- Avoidance of vandalism
If you are interested in IoT video surveillance, here you can find more information on how smart video systems enable data analysis, are used in communities in combination with other IoT applications and reduce the existing risks in temporary locations.
Elevator emergency call
Never been stuck in an elevator before? You are lucky! Such a situation often triggers anxiety and panic in the people affected. It is vital to get help quickly.
The elevator emergency call gives trapped persons the opportunity to call for external help via an integrated emergency call system so that they can leave the elevator as quickly as possible. Ideally, the emergency call system directs users to an emergency call center manned around the clock, which notifies the maintenance company in the event of a breakdown.
An elevator emergency call is now mandatory for elevators. These systems have to operate reliably even in the event of a power failure and similar situations.
For further information, you should contact your countries national safety standards organisation.
Fire alarm systems
Safety when things get hot: A fire alarm system is a hazard detection system in the field of preventive fire protection. A fire alarm control panel receives and evaluates events from various fire detectors and initiates appropriate actions.
Even under the extreme conditions caused by fire (high temperatures, destruction of data transmission systems, etc.), the fire alarm system must reliably forward the fire alarm to alert the local fire department.
There are also various other requirements for the fire alarm system and the fail-safe data transmission route:
- Triggering of an internal alarm to enable checks to be made to avoid false alarms
- Activating smoke extraction systems
- Control of elevators
- Closing fire protection barriers
- Triggering of a fire extinguishing system, e.g. CO₂ extinguishing system
A minimum number of regulations must be observed when installing and operating fire alarm systems. However, fire alarm systems installed with additional Smart IoT systems have significant potential cost advantages, for example they can reduce service and maintenance costs.
Monitoring of electronic POS systems through backup via mobile connection
No data transfer, no money! This is solved by an electronic checkout system with LTE backup feature. An electronic cash register system is an IT solution that adds additional functions to a conventional cash register.
The monitoring of electronic POS systems by means of a backup via mobile connection serves to maintain business operations and communication in the event of an internet outage or cable break. Such a system is commonly used in the hospitality and retail sectors and related industries.
In-service advantages are:
- No downtime and proactive damage prevention
- Maximum security through connectivity to several or even all LTE networks per country
- Individual and scalable solutions, independent of location
- Alternative transmission path for data transfer & communication
The coronavirus pandemic has had a significant impact on the development of digital standards, including the use of digital POS systems. You can find out more about these trends in the hospitality industry here.
IoT solutions in use: how do we measure success?
When the system and the IoT service are connected to each other and the regular system runs at an acceptable level or shows no impairment at all during the test, then the processes have been successfully protected.
Are you at the concept phase or part way through developing and installing new systems and equipment? Are you looking for the right partner to maintain fail-safe processes? Then FUSION IoT is waiting for you!
Flexible IoT solutions with fail-safe connectivity
Flexible IoT solutions enable device and system manufacturers and their customers to ensure process reliability and redundancy through connectivity.
FUSION IoT is a brand of Epsilon Telecommunications GmbH, part of the Gamma group, based in near the city of Hof in Germany. Thanks to many years of experience and our huge partner network, with extensive expertise in a wide range of industries, we can tailor-make the right solution for your needs and processes. We are the most successful German service provider for telecommunications in the B2B market.
Our advantages:
- Flexibility – in the content of the contract and after sales support
- Independence – through objective advice and a broad portfolio of products and services with different network operators
- Expand your German markets – access to the large SME partner network of Epsilon Telecom and FUSION IoT
Are you looking for the route to reliability for your products and services or do you need to make your company’s systems fail-safe?
We offer you the crucial connectivity and systems together with our partners. One example: LTE Backup as a complete package to secure the primary Internet connection for security-relevant applications.
Do you offer security systems services and security technology, and do you want to make them smarter with IoT solutions or optimize your existing products and services? We listen and work with you to develop your ideas and products into market-ready IoT solutions. You can also benefit from extended market access to German markets through our broad network of partners in the German SME sector.
AUTHOR

Florian Sonntag
FUSION IoT
Head of Project Management FUSION IoT
Do you have questions about the article?